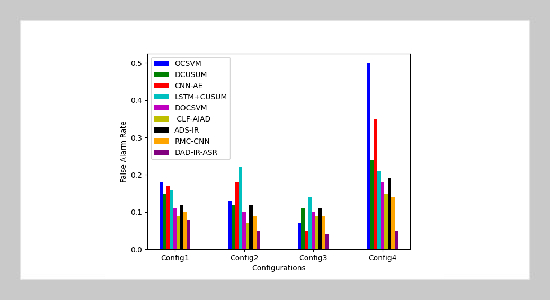
- [1] S. Yin, (2023) “Object Detection Based on Deep Learning: A Brief Review" IJLAI Transactions on Science and Engineering 1(02): 1–6.
- [2] J. Gao, M. Liu, P. Li, J. N. Zhang, and Z. K. Chen, (2023) “Deep Multiview Adaptive Clustering With Se�mantic Invariance" IEEE Trans. Neural Netw. Learn. Syst. DOI: 10.1109/TNNLS.2023.3265699.
- [3] P. Li, A. A. Laghari, M. Rashid, J. Gao, T. R. Gadekallu, A. R. Javed, and S. Yin, (2023) “A Deep Multimodal Adversarial Cycle-Consistent Network for Smart Enterprise System" IEEE Transactions on In�dustrial Informatics 19(1): 693–702. DOI: 10.1109/TII.2022.3197201.
- [4] I. Kotenko, K. Izrailov, and M. Buinevich, (2022) “Static analysis of information systems for IoT cyber secu�rity: a survey of machine learning approaches" Sensors 22(4): 1335. DOI: 10.3390/s22041335.
- [5] P. Li, J. Gao, J. N. Zhang, S. Jin, and Z. K. Chen, (2022) “Deep Reinforcement Clustering" IEEE Trans. Multime�dia: DOI: 10.1109/TMM.2022.3233249.
- [6] L. Teng, (2023) “Brief Review of Medical Image Segmen�tation Based on Deep Learning" IJLAI Transactions on Science and Engineering 1(02): 01–08.
- [7] M. Mukhasheva, K. Ybyraimzhanov, K. Naubaeva, A. Mamekova, and B. Almukhambetova, (2023) “The Impact of Educational Robotics on Cognitive Outcomes in Primary Students: A Meta-Analysis of Recent Studies." European Journal of Educational Research 12(4): DOI: 10.12973/eu-jer.12.4.1683.
- [8] A. Modli´nski, P. Fortuna, and B. Roznowski, (2023) ˙ “Human–machine trans roles conflict in the organization: How sensitive are customers to intelligent robots replac�ing the human workforce?" International Journal of Consumer Studies 47(1): 100–117. DOI: 10.1111/ijcs.12811.
- [9] H. Alemzadeh, D. Chen, X. Li, T. Kesavadas, Z. T. Kalbarczyk, and R. K. Iyer. “Targeted attacks on teleoperated surgical robots: Dynamic model-based detection and mitigation”. In: 2016 46th Annual IEEE/IFIP International Conference on Dependable Sys�tems and Networks (DSN). IEEE. 2016, 395–406. DOI: 10.1109/DSN.2016.43.
- [10] Y. Tang, D. Zhang, D. W. Ho, W. Yang, and B. Wang, (2018) “Event-based tracking control of mobile robot with denial-of-service attacks" IEEE Transactions on Sys�tems, Man, and Cybernetics: Systems 50(9): 3300–3310. DOI: 10.1109/TSMC.2018.2875793.
- [11] C. Zhou, B. Hu, Y. Shi, Y.-C. Tian, X. Li, and Y. Zhao, (2020) “A unified architectural approach for cyberattack�resilient industrial control systems" Proceedings of the IEEE 109(4): 517–541. DOI: 10.1109/JPROC.2020.3034595.
- [12] E. Khalastchi, M. Kalech, G. A. Kaminka, and R. Lin, (2015) “Online data-driven anomaly detection in autonomous robots" Knowledge and Information Sys�tems 43: 657–688. DOI: 10.1007/s10115-014-0754-y.
- [13] F. Angiulli and C. Pizzuti. “Fast outlier detection in high dimensional spaces”. In: European conference on principles of data mining and knowledge discovery. Springer. 2002, 15–27. DOI: 10.1007/3-540-45681-3_2.
- [14] H. Xu, W. Chen, N. Zhao, Z. Li, J. Bu, Z. Li, Y. Liu, Y. Zhao, D. Pei, Y. Feng, et al. “Unsupervised anomaly detection via variational auto-encoder for seasonal kpis in web applications”. In: Proceedings of the 2018 world wide web conference. 2018, 187–196. DOI: 10.1145/3178876.3185996.
- [15] C. Zhou, S. Huang, N. Xiong, S.-H. Yang, H. Li, Y. Qin, and X. Li, (2015) “Design and analysis of multimodel�based anomaly intrusion detection systems in industrial process automation" IEEE Transactions on Systems, Man, and Cybernetics: Systems 45(10): 1345–1360. DOI: 10.1109/TSMC.2015.2415763.
- [16] A. A. Jaber and R. Bicker, (2016) “Industrial robot fault detection based on statistical control chart" Am. J. Eng. Applied Sci 9: 251–263.
- [17] V. Sathish, S. Ramaswamy, and S. Butail, (2016) “Training data selection criteria for detecting failures in industrial robots" IFAC-PapersOnLine 49(1): 385–390. DOI: 10.1016/j.ifacol.2016.03.084.
- [18] Y. Zhao and C. Smidts, (2020) “A control-theoretic ap�proach to detecting and distinguishing replay attacks from other anomalies in nuclear power plants" Progress in Nuclear Energy 123: 103315. DOI: 10.1016/j.pnucene.2020.103315.
- [19] W. Zhu, W. Li, H. Liao, and J. Luo, (2021) “Temperature network for few-shot learning with distribution-aware large-margin metric" Pattern Recognition 112: 107797. DOI: 10.1016/j.patcog.2020.107797.
- [20] Y. Zhou, L. Xie, and H. Pan, (2022) “Research on a PSO�H-SVM-Based Intrusion Detection Method for Industrial Robotic Arms" Applied Sciences 12(6): 2765. DOI: 10.3390/app12062765.
- [21] J. Inoue, Y. Yamagata, Y. Chen, C. M. Poskitt, and J. Sun. “Anomaly detection for a water treatment system using unsupervised machine learning”. In: 2017 IEEE international conference on data mining work�shops (ICDMW). IEEE. 2017, 1058–1065. DOI: 10.1109/ICDMW.2017.149.
- [22] Ö. Gültekin, E. Cinar, K. Özkan, and A. Yazıcı, (2022) “Real-time fault detection and condition monitoring for industrial autonomous transfer vehicles utilizing edge ar�tificial intelligence" Sensors 22(9): 3208. DOI: 10.3390/s22093208.
- [23] A. Munawar, P. Vinayavekhin, and G. De Magistris. “Spatio-temporal anomaly detection for industrial robots through prediction in unsupervised feature space”. In: 2017 IEEE Winter Conference on Applica�tions of Computer Vision (WACV). IEEE. 2017, 1017–1025. DOI: 10.1109/WACV.2017.118.
- [24] M. Said Elsayed, N.-A. Le-Khac, S. Dev, and A. D. Jurcut. “Network anomaly detection using LSTM based autoencoder”. In: Proceedings of the 16th ACM Symposium on QoS and Security for Wireless and Mobile Networks. 2020, 37–45. DOI: 10.1145/3416013.3426457.
- [25] L. Mhamdi, D. McLernon, F. El-Moussa, S. A. R. Zaidi, M. Ghogho, and T. Tang. “A deep learning ap�proach combining autoencoder with one-class SVM for DDoS attack detection in SDNs”. In: 2020 IEEE Eighth International Conference on Communications and Networking (ComNet). IEEE. 2020, 1–6. DOI: 10.1109/ComNet47917.2020.9306073.
- [26] A. Binbusayyis and T. Vaiyapuri, (2021) “Unsuper�vised deep learning approach for network intrusion detec�tion combining convolutional autoencoder and one-class SVM" Applied Intelligence 51(10): 7094–7108. DOI: 10.1007/s10489-021-02205-9.
- [27] E. Mushtaq, A. Zameer, M. Umer, and A. A. Abbasi, (2022) “A two-stage intrusion detection system with auto�encoder and LSTMs" Applied Soft Computing 121: 108768. DOI: 10.1016/j.asoc.2022.108768.
- [28] K. Hundman, V. Constantinou, C. Laporte, I. Colwell, and T. Soderstrom. “Detecting spacecraft anomalies using lstms and nonparametric dynamic threshold�ing”. In: Proceedings of the 24th ACM SIGKDD interna�tional conference on knowledge discovery & data mining. 2018, 387–395. DOI: 10.1145/3219819.3219845.
- [29] C. Yukawa, K. Toyoshima, Y. Nagai, M. Niihara, Y. Yamashita, T. Oda, and L. Barolli. “An Anomaly De�tection System for Intelligent Robot Vision Using LSTM”. In: International Conference on Advanced In�formation Networking and Applications. Springer. 2023, 192–198. DOI: 10.1007/978-3-031-28451-9_17.
- [30] Z. Liu, Y. Hou, H. Tang, Á. López-Chilet, S. Michiels, D. Botteldooren, J. A. Gómez, and D. Hughes. “CLF-AIAD: A Contrastive Learning Framework for Acoustic Industrial Anomaly Detection”. In: Inter�national Conference on Neural Information Processing. 2023, 125–137. DOI: 10.1007/978-981-99-8126-7_10.
- [31] K. S. Sankaran and B.-H. Kim, (2023) “Deep learn�ing based energy efficient optimal RMC-CNN model for secured data transmission and anomaly detection in in�dustrial IOT" Sustainable Energy Technologies and Assessments 56: 102983. DOI: 10.1016/j.seta.2022.102983.