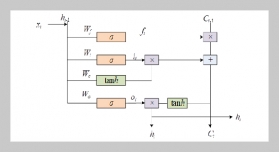
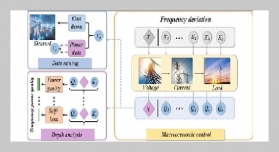
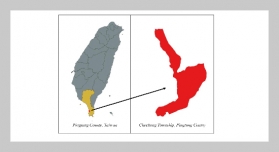
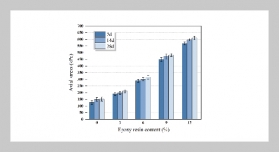
REFERENCES
- [1] Fragouli, C., Prabhakaran, V. M., Czap, L. and Diggavi, S. N., “Wireless Network Security: Building on Erasures,” Proceedings of the IEEE, Vol. 103, No. 10, pp. 18261840 (2015). doi: 10.1109/JPROC.2015.24383 12
- [2] Saeed, M., et al., “A Secure Two-party Password-authenticated Key Exchange Protocol,” Proc. 2014 IEEE 15th Int’l Conf. on Information Reuse and Integration, pp. 466474 (2014). doi: 10.1109/IRI.2014.70 51926
- [3] Lin, Y., Hou, M. and Xu, Q., “Strongly PasswordBased Three-Party Authenticated Key Exchange Protocol,” Proc. 2013 9th Int’l Conf. on Computational Intelligence and Security, pp. 555558 (2013). doi: 10. 1109/CIS.2013.123
- [4] Byun, J. W., Jeong, I. R., Lee, D. H. and Park, C.-S., “Password-Authenticated Key Exchange between Clients with Different Passwords,” Proc. 4th Int’l Conf. on Information and Communications Security, LNCS 2513, pp. 134146 (2002). doi: 10.1007/3-540-36159- 6_12
- [5] Feng, D.-G. and Xu, J., “A New Client-to-Client Password-Authenticated Key Agreement Protocol,” Proc. 2nd Int’l Workshop on Coding and Cryptology, LNCS 5557, pp. 6376 (2009). doi: 10.1007/978-3-642-01877- 0_7
- [6] Jin, W. and Xu, J., “An Efficient and Provably Secure Cross-Realm Client-to-Client Password-Authenticated Key Agreement Protocol with Smart Cards,” Proc. 8th Int’l Conf. on Cryptology and Network, LNCS 5888, pp. 299314 (2009). doi: 10.1007/978-3-642-10433- 6_20
- [7] Yau, W.-C., Phan, R. C.-W., Goi, B.-M. and Heng, S.-H., “Cryptanalysis of a Provably Secure Cross-Realm Client-to-Client Password-Authenticated Key Agreement Protocol of CANS ’09,” Proc. 10th Int’l Conf. on Cryptology and Network, LNCS 7092, pp. 172184 (2011). doi: 10.1007/978-3-642-25513-7_13
- [8] Ding, X. and Ma, C., “Cryptoanalysis and Improvements of Cross-Realm C2C-PAKE Protocol,” Proc. 2009 WASE Int’l Conf. on Information Engineering, pp. 193196 (2009). doi: 10.1109/ICIE.2009.39
- [9] Yoneyama, K., “Efficient and Strongly Secure Password-Based Server Aided Key Exchange,” Proc. 9th Int’l Conf. on Cryptology in India, LNCS 5365, pp. 172184 (2008). doi: 10.1007/978-3-540-89754-5_14
- [10] Abdalla, M., Fouque, P.-A. and Pointcheval, D., “Password-Based Authenticated Key Exchange in the ThreeParty Setting,” Proc. 2005 Int’l Conf. on Public Key Cryptography, LNCS 3386, pp. 6584 (2005). doi: 10. 1007/978-3-540-30580-4_6
- [11] Bellare, M., Pointcheval, D. and Rogaway, P., “Authenticated Key Exchange Secure Against Dictionary Attacks,” Proc. 2000 Int’l Conf. on the Theory and Application of Cryptographic Techniques, LNCS 1807, pp. 140156 (2000).
- [12] Bellare, M. and Rogaway, P., “Entity Authentication and Key Distribution,” Advances in Cryptology - CRYPTO 93, LNCS 773, pp. 232249 (1994). doi: 10.1007/3-540-48329-2_21
- [13] Bellare, M. and Rogaway, P., “Provably Secure Session Key Distribution - The Three Party Case,” Proc. 28th Annual ACM Symp. on Theory of Computing, pp. 5766 (1996).
- [14] Canetti, R. and Krawczyk, H., “Analysis of Key-Exchange Protocols and Their Use for Building Secure Channels,” Proc. 2001 Int’l Conf. on Advances in Cryptology, pp. 451472 (2001). doi: 10.1007/3-540-44987- 6_28
- [15] Krawczyk, H., “HMQV: a High-Performance Secure Diffie-Hellman Protocol,” Proc. 25th Annual Int’l Cryptology Conf., LNCS 3621, pp. 546566 (2005).
- [16] Wardlow, W. P., “The RSA Public Key Cryptosystem,” Proc. 1991 Int’l Conf. con Coding Theory and Cryptography, pp. 101124 (1991).
- [17] Daemen, J. and Rijmen, V., The Design of Rijndael: AES - The Advanced Encryption Standard, SpringerVerlag (2002).
- [18] Wang, X., Yin, Y. and Yu, H., “Finding Collisions in the Full SHA-1,” Proc. 25th Annual Int’l Cryptology Conf., LNCS 3621, pp. 1736 (2005).
- [19] Coffee, T., “Best Kept Secrets: Elliptic Curves and Modern Cryptosystems,” MIT 18.704, Fall (2004).
- [20] Boneh, D., “The Decision Diffie-Hellman Problem,” Proc. 3rd Algorithmic Number Theory Symp., LNCS 1423, pp. 4863 (1998). doi: 10.1007/BFb0054851
- [21] Rivest, R. L., “RFC 1321: The MD5 Message-Digest Algorithm,” Technical Report, Internet Activities Board, April (1992).
- [22] Yi, X., Ling, S. and Wang, H., “Efficient Two-Server Password-Only Authenticated Key Exchange,” IEEE Trans. on Parallel and Distributed Systems, Vol. 24, No. 9, pp. 17731782 (2013). doi: 10.1109/TPDS.2012. 282