Shuguang Zhang This email address is being protected from spambots. You need JavaScript enabled to view it.1,2, Xuehai Zhou2 , Feng Yang2 and Jun Xu2 1School of Electronics and Information Engineering, Anhui JianZhu University, Hefei, P.R. China
2School of Computer Science and Technology, University of Science and Technology of China, Hefei, P.R. China
Received:
July 9, 2015
Accepted:
September 7, 2015
Publication Date:
December 1, 2015
Download Citation:
||https://doi.org/10.6180/jase.2015.18.4.11
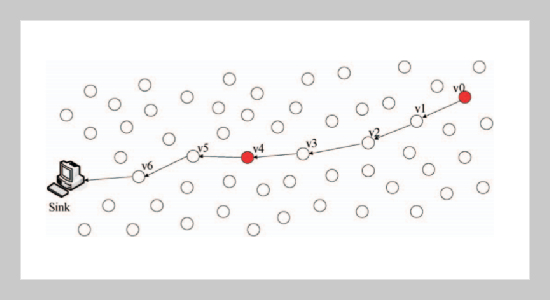
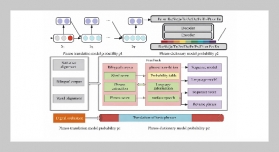
The false data injection attack has been regarded as a significant challenge in wireless sensor networks. Malicious nodes could launch false data injection attacks by sending a lot of forged packets, in order to exhaust network resources and influence the user decision. In order to efficiently locate the malicious nodes, this paper proposes an edge marking strategy based on two-hop neighbor information. Sensor nodes are divided into two types marking nodes and non-marking nodes in this method, and only marking nodes need to mark packets with certain probability. The Sink nodes will trace the malicious nodes by using the received traceback information of packet marking. Theoretical analysis and experimental results demonstrate that the strategy only needs the marking nodes to reconstruct the attack path. Furthermore, due to the reason that the path between adjacent marking nodes can be obtained by two-hop neighbor information, the reconstruction attack path length is reduced to 50% of traditional methods, and the number of packets needed is greatly reduced.ABSTRACT
Keywords:
Wireless Sensor Network, Two-Hop Neighbor Information, Traceback, Probabilistic Edge Marking
REFERENCES