Hsing-Chung Chen1,2, Chuan-Hsien Mao1 and Shian-Shyong Tseng This email address is being protected from spambots. You need JavaScript enabled to view it.3 1Department of Computer Science and Information Engineering, Asia University, Taichung, Taiwan 413, R.O.C.
2Department of Medical Research, China Medical University Hospital, China Medical University, Taichung, Taiwan 404, R.O.C.
3Department of Applied Informatics and Multimedia, Asia University, Taichung, Taiwan 413, R.O.C.
Received:
June 3, 2014
Accepted:
January 22, 2015
Publication Date:
March 1, 2015
Download Citation:
||https://doi.org/10.6180/jase.2015.18.1.10
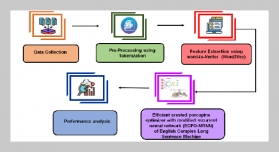
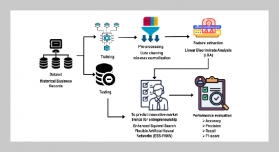
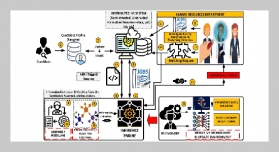
In recent years, there have been many approaches proposed by many researchers to detect RTT (round-trip time) and RTO (retransmission timeout) message traffic accessing email and trying to determine whether these belong to dangerous traffic. The aim of this study is to protect an electronic mail (email) server system based on the integrated entropy calculations of the multiple protocols of RTT and RTO in order to detect flooding attacks. Entropy is an approach in the mathematical theory of communication. It can be used to measure the uncertainty or randomness in a random variable. A normal email server usually supports four protocols consisting of simple mail transfer protocol (SMTP), post office protocol version 3 (POP3), Internet Message Access Protocol version 4 (IMAP4), and HTTPS being used by a remote web-based email. However, in the internet, there are many flooding attacks that attempt to paralyze an email server system. Therefore, we propose a new approach for detecting flooding attacks based on the integrated entropy measurements for an email server. Our approach can reduce the misjudged rate compared to conventional approaches.ABSTRACT
Keywords:
Entropy, Flooding Attack, E-mail Server, RTT, RTO
REFERENCES


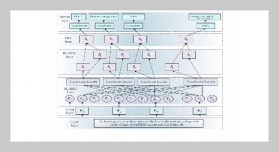
![The SMTP architecture [1,2,4]. An Approach for Detecting a Flooding Attack Based on Entropy Measurement of Multiple E-Mail Protocols](/images/article_images/18/18_1_10.jpg)