REFERENCES
- [1] Garcia-Hernández, C. F., Ibargengoytia González, P. H., Garcia Hernández, J. and Perez Díaz, J. A., “Wireless Sensor Networks and Applications: A Survey,” International Journal of Computer Science and Network Security, Vol. 3, pp. 264�273 (2007).
- [2] Holger Karl and Andreas Willig, Protocols and Architectures for Wireless Sensor Networks, John Wiley & Sons Ltd, England (2005).
- [3] Balzano, L., “Addressing Fault and Calibration in Sensor Networks,” Master’s Thesis, Dept. of Computer Science, UCLA (2007).
- [4] Sharma, A., Golubchik, L. and Govindan, R., “On the Prevalence of Sensor Faults in Real-World Deployments,” 4th Annual IEEE Communications Society Conference on Sensor, Mesh and Adhoc Communications and Networks, San Diego, CA, pp. 213�222 (2007). doi: 10.1109/SAHCN.2007.4292833
- [5] Ni, K., Nithya Ramanathan, Mohammed Nabil Hajj Chehade, Laura Balzano, Sheela Nair, Sadaf Zahedi, Eddie Kohler, Greg Pottie, Mark Hansen and Mani Srivastava, “Sensor Network Data Fault Types,” ACM Trans. on Sensor Networks, Vol. 5, No. 3 (2009). doi: 10.1145/1525856.1525863
- [6] Han, J. and Kamber, M., “Data Mining: Concepts and Techniques,” Second Edition, San Francisco, Morgan Kaufmann (2006).
- [7] Hodge, V. and Austin, J., “A Survey of Outlier Detection Methodologies,” Journal of Artificial Intelligence Review, Vol. 22, No. 2, pp. 85�126 (2004). doi: 10. 1007/s10462-004-4304-y
- [8] Yang Zhang Meratnia and Havinga, P., “Outlier Detection Techniques for Wireless Sensor Networks: A Survey,” IEEE Communication Surveys & Tutorials, Vol. 12, No. 2, pp. 159�170 (2010). doi: 10.1109/SURV. 2010.021510.00088
- [9] Hung, T. P. and Han Y. S., “Power Efficient Direct Voting Assurance for Data Fusion in Wireless Sensor Networks,” IEEE Transactions on Computers, Vol. 57, No. 2, pp. 261�273 (2008). doi: 10.1109/TC.2007. 70805
- [10] Zhang, Q., Yu, T. and Ning, P., “A Framework for Identifying Compromised Nodes in Wireless Sensor Networks,” ACM Transactions on Information and Systems Security, Vol. 11, Article No. 12 (2008). doi: 10.1145/1341731.1341733
- [11] Wu, W., Cheng, X., Ding, M., Xing, K., Liu, F. and Deng, P., “Localized Outlying and Boundary Data Detection in Sensor Networks,” IEEE Transactions on Knowledge and Data Engineering, Vol. 19, No. 8, pp. 1145� 1157 (2007). doi: 10.1109/TKDE.2007.1067
- [12] Antonios Deligiannakis, Vassilis Stoumpos, Yannis Kotidis, Vasilis Vassalos, Alex Delis, “Outlier-Aware Data Aggregation in Sensor Networks,” IEEE 24th International Conference on Data Engineering (ICDE’08), Washington, DC, USA, pp. 1448�1450 (2008). doi: 10.1109/ICDE.2008.4497585
- [13] Rajasegarar, S., Bezdek, J. C., Leckie, C. and Palaniswami, M., “Elliptical Anomalies in Wireless Sensor Networks,” ACM Transactions on Sensor Networks (ACM TOSN), Vol. 6, No. 1 (2009). doi: 10. 1145/1653760.1653767
- [14] Rajasegarar, S., Leckie, C. and Palaniswami, M., “Anomaly Detection in Wireless Sensor Networks,” IEEE Wireless Communications, Vol. 15, No. 4, pp. 34�40 (2008).
- [15] Di Pietro, R., Mancini, L. V., Soriente, C., Spognardi, A. and Tsudik, G., “Data Security in Unattended Wireless Sensor Networks,” IEEE Transaction on Computers, Vol. 58, No. 11, pp. 1500�1511 (2009). doi: 10.1109/TC.2009.109
- [16] Xie, Y. X., Chen, X. G. and Zhao, J., “Data Fault Detection for Wireless Sensor Networks Using Multi Scale PCA Method,” 2nd International Conference on Artificial Intelligence and Management Science and Electronic Commerce, Deng Leng, pp. 7035�7038 (2011). doi: 10.1109/AIMSEC.2011.6009921
- [17] Branch, J., Szymanski, B., Giannella, C. and Wol, R., “In-Network Outlier Detection in Wireless Sensor Networks,” 26th IEEE International Conference on Distributed Computing Systems, New York, p. 51 (2006). doi: 10.1109/ICDCS.2006.49
- [18] Sheng, B., Li, Q., Mao, W. and Jin, W., “Outlier Detection in Sensor Networks,” 8th ACM International Symposium on Mobile and Adhoc Networking and Computing, Canada, pp. 219�228 (2007). doi: 10.1145/ 1288107.1288137
- [19] Ren, S. Q. and Park, J. S., “Density Mining Based Resilient Data Aggregation for Wireless Sensor Networks,” 4th International Conference on Networked Computing and Advanced Information Management, pp. 261�266 (2008). doi: 10.1109/NCM.2008.92
- [20] Palpanas, T., Papadopoulos, D., Kalogeraki, V. and Gunopulos, D., “Distributed Deviation Detection in Sensor Networks,” ACM Special Interest Group on Management of Data, Vol. 32, No. 4, pp. 77�82 (2003). doi: 10.1145/959060.959074
- [21] Subramaniam, S., Palpanas, T., Papadopoulos, D., Kalogerakiand, V. and Gunopulos, D., “Online Outlier Detection in Sensor Data using Non-Parametric Models,” 32nd International Conference on Very Large Data Bases, Seoul, Korea,VLDB Endowment ACM, pp. 187�198 (2006).
- [22] Ganeriwal, S., Balzano, L. K. and Srivastava, M. B., “Reputation-Based Framework for High Integrity Sensor Networks,” ACM Transactions on Sensor Networks, Vol. 4, No. 3, pp. 1�37 (2008). doi: 10.1145/ 1362542.1362546
- [23] Papadimitriou, S., Kitagawa, H., Gibbons, P. B. and Faloutsos, C., “LOCI: Fast Outlier Detection Using the Local Correlation Integral,” Nineteenth International Conference on Data Engineering, Pittsburgh, pp. 315�326 (2003). doi: 10.1109/ICDE.2003.1260802
- [24] Kumar Samparthi, V. S. and Verma, H. K., “Outlier Detection of Data in Wireless Sensor Networks Using Kernel Density Estimation,” International Journal of Computer Applications, Vol. 5, No. 7, pp. 28�32 (2010). doi: 10.5120/924-1302
- [25] Breunig, M. M., Kriegel, H. P., Ng, R. T. and Sander, J., “LOF: Identifying Density-Based Local Outliers,” ACM SIGMOD International Conference on Management of Data, Dalles, TX, pp. 93�104 (2000). doi: 10.1145/335191.335388
- [26] Chiu, A. L. M. and Fu, A. W., “Enhancements on Local Outlier Detection,” IEEE Seventh International Database Engineering and Applications Symposium, China, pp. 298�307 (2003). doi: 10.1109/IDEAS. 2003.1214939
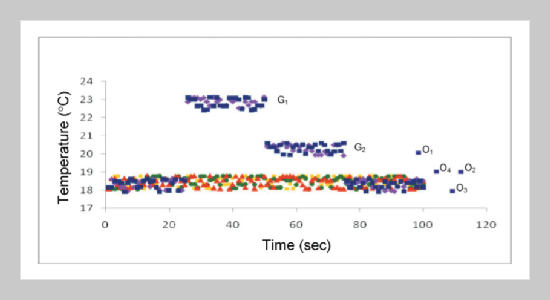
- [27] Intel Berkeley Research Laboratory, 2004, http://db. csail.mit.edu/labdata/labdata.html.