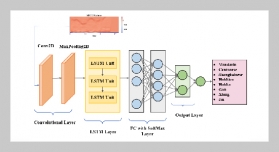
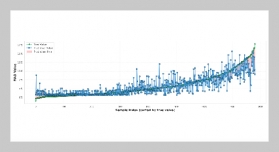
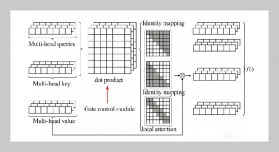
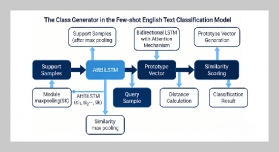
REFERENCES
- [1] Diffie, W. and Hellman, M., “New Directions in Cryptography,” IEEE Transactions on Information Theory, Vol. 22, pp. 644�654 (1976).
- [2] Chaum, D. and Heyst, E. V., “Group Signatures,” Advances in Cryptology-Eurocrypt’91, LNCS 547, Springer Verlag, New York, pp. 257�265 (1991).
- [3] Lee, C.-C., Chang, T.-Y. and Hwang, M.-S., “A New Group Signature Scheme Based on the Discrete Logarithm,” Journal of Information Assurance and Security, Vol. 5, pp. 54�57 (2010).
- [4] Rivest, R. L., Shamir, A. and Tauman, Y., “How to Leak a Secret,” Advances in Cryptology-ASIACRYPT 2001, LNCS 2248, Springer-Verlag, Berlin, pp. 552� 565 (2001).
- [5] Bresson, E., Stern, J. and Szydlo, M., “Threshold Ring Signatures and Applications to Ad-Hoc Groups,” Advances in Cryptology-CRYPTO’02, LNCS 2442, Spring-Verlag, Berlin, pp. 465�480 (2002).
- [6] Zhang, F. and Kim, K., “ID-Based Blind Signature and Ring Signature from Pairings,” Advance in Cryptology-ASIACRYPT 2002, LNCS 2501, Springer-Verlag, Berlin, pp. 629�637 (2002).
- [7] Liu, J. K., Wei, V. K. and Wong, D. S.,“Linkable Spontaneous Anonymous Group Signature for Ad Hoc Groups,” Information Security and Privacy, LNCS 3108, Springer Verlag, Berlin, pp. 325�335 (2004).
- [8] Lee, K.-C., Wen, H.-A. and Hwang, T., “Convertible Ring Signature,” Communications, IEE Proceedings, Vol. 152, pp. 411�414 (2005).
- [9] Ren, J. and Harn, L., “Generalized Ring Signature,” IEEE Transactions on Dependable and Secure Computing, Vol. 5, pp. 155�163 (2008).
- [10] Wang, H., Zhang, F. and Sun, Y., “Cryptanalysis of a Generalized Ring Signature Scheme,” IEEE Transactions on Dependable and Secure Computing, Vol. 6, pp. 149�151 (2009).
- [11] Xiong, H., Qin, Z. and Li, F., “An Anonymous Sealed-Bid Electronic Auction Based on Ring Signature Scheme,” International Journal of Network Security, Vol. 8, pp. 235�242 (2009).
- [12] Jakobsson, M., Sako, K. and Impagliazzo, R., “Designated Verifier Proofs and Their Applications,” Advances in Cryptology-Eurocrypt’96, LNCS 1070, Springer Verlag, Berlin, pp. 143�154 (1996).
- [13] Saeednia, S., Kremer, S. and Markowitch, O., “An Efficient Strong Designated Verifier Signature Scheme,” Information Security and Cryptology-INCISC 2003, LNCS 2971, Springer-Verlag, Berlin, pp. 40�54 (2003).
- [14] Lee, J. S. and Chang, J. H., “Strong Designated Verifier Ring Signature Scheme,” Innovations and Advanced Techniques in Computer and Information Sciences and Engineering, Springer-Verlag, Netherlands, pp. 543�547 (2007).
- [15] Wu, L. and Li, D., “Strong Designated Verifier IDBased Ring Signature Scheme,” Information Science and Engineering, 2008, ISISE’08, International Symposium, Vol. 1, Shanghai, P.R.O.C., Dec. 20�22, pp. 294�298 (2008).
- [16] Hwang, S.-J. and Cheng, K.-L., “A Ring Signature Scheme with Strong Designated Verifiers to Provide Signer Anonymity,” Workshop on Cryptography and Information Security, NCS 2009, Taipei, Taiwan, R.O.C., Dec., pp. 58�69 (2009).
- [17] Cormen, T. H., Leiserson, C. E. and Rivest, R. L., Introduction to Algorithms, MIT Press, New York, (2001).