Chih-Hung Lin This email address is being protected from spambots. You need JavaScript enabled to view it.1 and Wen-Shyong Hsieh1,2 1Department of Computer Science and Engineering, National Sun Yat-sen University, Kaohsiung, Taiwan 804, R.O.C.
2Department of Computer Science and Information Engineering, Shu Te University, Kaohsiung, Taiwan 824, R.O.C.
Received:
January 13, 2005
Accepted:
November 2, 2005
Publication Date:
June 1, 2006
Download Citation:
||https://doi.org/10.6180/jase.2006.9.2.01
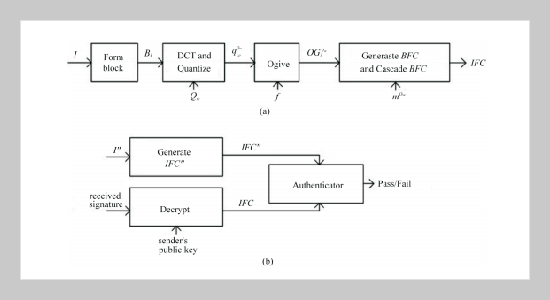
Semi-fragile image authentication methods are robust to JPEG images, but are fragile to other malicious manipulations. This paper presents a novel digital signature scheme that adopts statistic Ogive analysis in quantized discrete cosine transform (DCT) coefficients to construct a feature code for image authentication. The lower bound sensitivity of fragility can be determined by a predetermined degree of fragility corresponding to an acceptable JPEG compression quality factor. The degree of fragility can be easily adjusted by simply controlling a fragile degree factor (FDF). This paper analyzes how to choose FDF and the critical image feature properties. Experimental results indicate the effectiveness of the proposed method.ABSTRACT
Keywords:
Digital Signature, Image Authentication, JPEG, Ogive, Semi-Fragile
REFERENCES