Fun Ye1 , Shiann-Tsong Sheu This email address is being protected from spambots. You need JavaScript enabled to view it.1 , Tobias Chen1 and Jenhui Chen2 1Department of Electrical Engineering Tamkang University Tamsui,Taiwan 251, R.O.C.
2Department of Computer Science and Information Engineering Tamkang University Tamsui, Taiwan 251, R.O.C.
Received:
October 1, 2002
Accepted:
December 30, 2002
Publication Date:
March 1, 2003
Download Citation:
||https://doi.org/10.6180/jase.2003.6.1.08
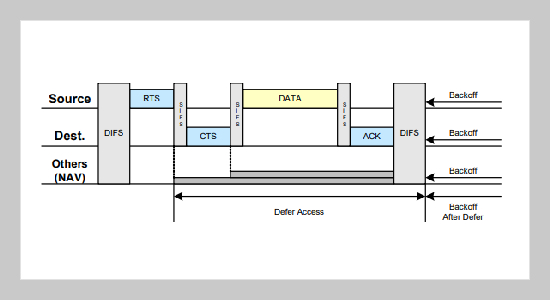
Wireless technologies and applications received great attention in recent years. The medium access control (MAC) protocol is the main element that determines the efficiency in sharing the limited communication bandwidth of the wireless channel in wireless local area networks (WLANs). The request-to-send/clear-to-send (RTS/CTS) mechanism is an optional handshaking procedure used by the IEEE 802.11 wireless network to reduce the possibility of collision. The RTS_Threshold (RT) value which determines when the RTS/CTS handshaking mechanism should be used is an important parameter to investigate; since different RT values will produce different performance characteristics in data transmission. This paper presents an evaluation of the influence of the RT parameter on the IEEE 802.11 wireless network, and gives a guideline to dynamically adjust the RT value. Simulation results of this paper show that, in order to achieve the best performance, the RT should be dynamically adjusted according to the environment. However, we suggest to have the RTS/CTS always activated (RT = 0), saving complex work designing and implementing a dynamic RT mechanism, to obtain a near best performance.ABSTRACT
Keywords:
Ad Hoc, IEEE 802.11, MAC, RTS/CTS, Wireless
REFERENCES