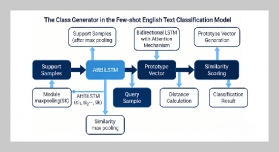
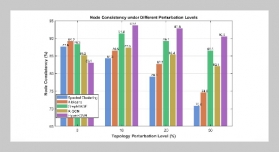
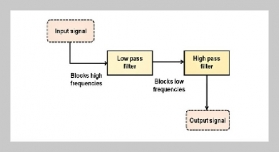
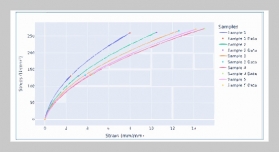
- [1] E. Rodriguez, B. Otero, and R. Canal, (2023) “A sur vey of machine and deep learning methods for privacy protection in the internet of things" Sensors 23(3): 1252. DOI: 10.3390/s23031252.
- [2] A. Brauneck, L. Schmalhorst, M. M. Kazemi Majd abadi, M. Bakhtiari, U. Völker, J. Baumbach, L. Baum bach, and G. Buchholtz, (2023) “Federated machine learning, privacy-enhancing technologies, and data pro tection laws in medical research: scoping review" Jour nal of Medical Internet Research 25: e41588. DOI: 10.2196/41588.
- [3] Y. Wang and L. Sun, (2024) “Privacy Protection of Secure Sharing Electronic Health Records Based on Blockchain." International Journal of Advanced Computer Science & Applications 15(7): DOI: 10.14569/IJACSA.2024.0150791.
- [4] S. Yin, H. Li, A. A. Laghari, T. R. Gadekallu, G. A. Sampedro, and A. Almadhor, (2024) “An anomaly detection model based on deep auto-encoder and capsule graph convolution via sparrow search algorithm in 6G internet-of-everything" IEEE Internet of Things Jour nal 11(18): 29402–29411. DOI: 10.1109/JIOT.2024.3353337.
- [5] M. Al-Hawawreh and M. S. Hossain, (2023) “A privacy-aware framework for detecting cyber attacks on internet of medical things systems using data fusion and quantum deep learning" Information Fusion 99: 101889. DOI: 10.1016/j.inffus.2023.101889.
- [6] H. B. Mahajan and A. A. Junnarkar, (2023) “Smart healthcare system using integrated and lightweight ECC with private blockchain for multimedia medical data pro cessing" Multimedia Tools and Applications 82(28): 44335–44358. DOI: 10.1007/s11042-023-15204-4.
- [7] J.Miao,Z.Wang,Z.Wu,X.Ning,andP.Tiwari,(2024) “A blockchain-enabled privacy-preserving authentication management protocol for Internet of Medical Things" Expert Systems with Applications 237: 121329. DOI: 10.1016/j.eswa.2023.121329.
- [8] R.Praveen and P. Pabitha, (2023) “Improved Gentry Halevi’s fully homomorphic encryption-based lightweight privacy preserving scheme for securing medical Internet of Things" Transactions on Emerging Telecommuni cations Technologies 34(4): e4732. DOI: 10.1002/ett.4732.
- [9] S. Yin, H. Li, L. Teng, A. A. Laghari, and V. V. Estrela, (2024) “Attribute-based multiparty searchable encryption model for privacy protection of text data" Multimedia Tools and Applications 83(15): 45881–45902. DOI: 10.1007/s11042-023-16818-4.
- [10] G.Zyskind,O.Nathan,etal.“Decentralizingprivacy: Using blockchain to protect personal data”. In: 2015 IEEE security and privacy workshops. IEEE. 2015, 180 184. DOI: 10.1109/SPW.2015.27.
- [11] Z. Xue, M. Wang, Q. Zhang, Y. Zhang, and P. Liu, (2021) “A regulatable blockchain transaction model with privacy protection" International Journal of Compu tational Intelligence Systems 14(1): 1642–1652. DOI: 10.2991/ijcis.d.210528.001.
- [12] S. Gao, Q. Su, R. Zhang, J. Zhu, Z. Sui, and J. Wang, (2021) “A Privacy-Preserving Identity Authentication Scheme Based on the Blockchain" Security and Commu nication Networks 2021(1): 9992353. DOI: 10.1155/2021/9992353.
- [13] W. Liang, Y. Yang, C. Yang, Y. Hu, S. Xie, K.-C. Li, andJ. Cao, (2022) “PDPChain: Aconsortium blockchain based privacy protection scheme for personal data" IEEE Transactions on Reliability 72(2): 586–598. DOI: 10.1109/TR.2022.3190932.
- [14] B. Faber, G. Michelet, N. Weidmann, R. R. Mukka mala, and R. Vatrapu. “BPDIMS: A blockchain-based personal data and identity management system”. In: The 52nd Hawaii International Conference on System Sci ences. HISS 2019: HISS 2019. Hawaii International Conference on System Sciences (HICSS). 2019, 6855 6864. DOI: 10125/60121.
- [15] Z. Lu, Q. Wang, G. Qu, H. Zhang, and Z. Liu, (2019) “A blockchain-based privacy-preserving authentication scheme for VANETs" IEEE Transactions on Very Large Scale Integration (VLSI) Systems 27(12): 2792–2801. DOI: 10.1109/TVLSI.2019.2929420.
- [16] J. Khan, S. Bhuiyan, G. Murphy, and J. Williams, (2016) “Data denoising and compression for smart grid communication" IEEE Transactions on signal and in formation processing over networks 2(2): 200–214. DOI: 10.1109/TSIPN.2016.2539680.
- [17] L. Teng, Y. Qiao, and S. Yin, (2024) “Underwater im age denoising based on curved wave filtering and two dimensional variational mode decomposition" Computer Science and Information Systems 21(4): 1765–1781. DOI: 10.2298/CSIS240314057T.
- [18] X. Yi, E. Walia, and P. Babyn, (2019) “Generative adver sarial network in medical imaging: A review" Medical image analysis 58: 101552. DOI: 10.1016/j.media.2019.101552.
- [19] L. Metz, B. Poole, D. Pfau, and J. Sohl-Dickstein, (2016) “Unrolled generative adversarial networks" arXiv preprint arXiv:1611.02163:
- [20] H. Liu, X. Luo, H. Liu, and X. Xia. “Merkle tree: A fundamental component of blockchains”. In: 2021 International Conference on Electronic Information En gineering and Computer Science (EIECS). IEEE. 2021, 556–561. DOI: 10.1109/EIECS53707.2021.9588047.
- [21] J. Xu, L. Wei, Y. Zhang, A. Wang, F. Zhou, and C.-z. Gao, (2018) “Dynamic fully homomorphic encryption based merkle tree for lightweight streaming authenticated data structures" Journal of Network and Computer Applications 107: 113–124. DOI: 10.1016/j.jnca.2018. 01.014.
- [22] H. Zhu, Y. Guo, and L. Zhang, (2021) “An improved convolution Merkle tree-based blockchain electronic medi cal record secure storage scheme" Journal of Informa tion Security and Applications 61: 102952. DOI: 10.1016/j.jisa.2021.102952.
- [23] O. Kuznetsov, A. Rusnak, A. Yezhov, K. Kuznetsova, D. Kanonik, and O. Domin, (2024) “Evaluating the security of Merkle trees: An analysis of data falsification probabilities" Cryptography 8(3): 33. DOI: 10.3390/ cryptography8030033.
- [24] X. Zhang, H. Zhong, J. Cui, I. Bolodurina, and L. Liu, (2022) “Lbvp: a lightweight batch verification protocol for fog-based vehicular networks using self-certified public key cryptography" IEEE Transactions on Vehicular Technology 71(5): 5519–5533. DOI: 10.1109/TVT.2022. 3157960.
- [25] M. Li, Z. Tian, X. Du, X. Yuan, C. Shan, and M. Guizani, (2023) “Power normalized cepstral robust fea tures of deep neural networks in a cloud computing data privacy protection scheme" Neurocomputing 518: 165 173. DOI: 10.1016/j.neucom.2022.11.001.
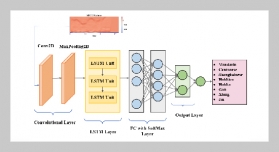
- [26] X. Li, H. Zhao, and W. Deng, (2023) “BFOD: Blockchain-based privacy protection and security shar ing scheme of flight operation data" IEEE Internet of Things Journal: DOI: 10.1109/JIOT.2023.3296460.
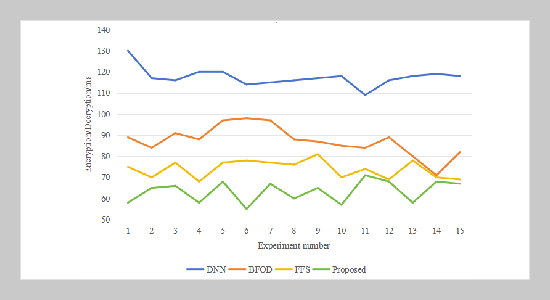
- [27] Y. Hu, Y. Zhang, X. Gao, D. Gong, X. Song, Y. Guo, and J. Wang, (2023) “A federated feature selection algo rithm based on particle swarm optimization under privacy protection" Knowledge-Based Systems 260: 110122. DOI: 10.1016/j.knosys.2022.110122.