Hai-Cheng Chu1 , Whe Dar Lin2 and Kuo-Hsiung Chang This email address is being protected from spambots. You need JavaScript enabled to view it.3 1Department of Information Management/International Business, Tunghai University, Taichung, Taiwan 407, R.O.C.
2Department of Accounting & Information Technology, The Overseas Chinese Institute of Technology, Taiwan, R.O.C.
3Department of International Business, Tunghai University, Taichung, Taiwan 407, R.O.C.
Received:
January 8, 2010
Accepted:
March 3, 2010
Publication Date:
March 3, 2010
Download Citation:
||https://doi.org/10.6180/jase.2010.13.1.10
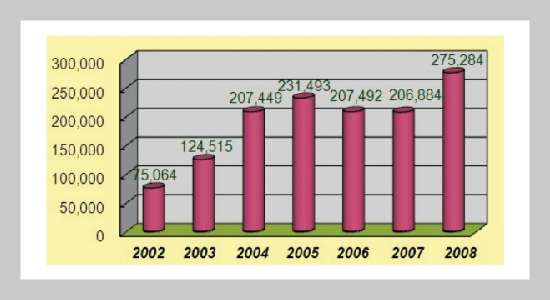
Due to the unprecedentedly ubiquitous wireless computer networks and mobile devices become prevalent, more unscrupulous technology hacktivists commit illegal conspiracies towards innocent victims via the ever growing Internet technology. Indeed, cybercrimes are relentlessly reported worldwide. The law enforcement agencies have the indispensable responsibility to crack the well-funded crime syndicate in our computer society. Consequently, Digital Forensics (DF) emerges and becomes the critical success factor to prosecute the culprit and prevent the associate cybercrime incidents from occurring. In the meanwhile, the computer society has an urgent demand for competent DF professionals to gather convincing digital evidences to assist indicting heinous perpetrators in order to allay the fears of everlasting computer crimes events in both private and public sectors. The research provides a vivid roadmap and suggested core curriculum design guidelines for higher education institutions to be integrated into their existing similar program or adopting as a groundbreaking reference model. A serial, cross-discipline, and functional approach were combined in order to design the suggested curriculum. Furthermore, the paper is attempting to minimize the theorypractice gap in DF and provide a milestone for higher education institutions to contemplate if necessary.ABSTRACT
Keywords:
Digital Forensics Core Curriculum, Cybercrime, Internet Technology, Exploited Security Leakage
REFERENCES