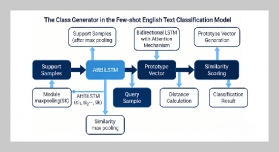
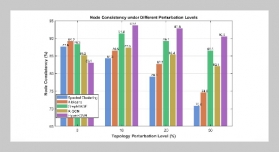
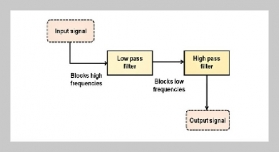
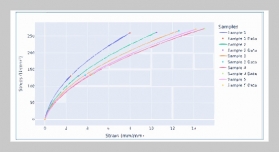
REFERENCES
- [1] El-Din, S. N. and Moniri, M., “Fragile and SemiFragile Image Authentication Based on Image SelfSimilarity,” IEEE International Conference on Image Processing, Vol. 2, pp. 22�25 (2002).
- [2] Friedman, G. L., “The Trustworthy Digital Camera: Restoring Credibility to the Photographic Image,” IEEE Trans. Consumer Electron., Vol. 39, pp. 905� 910 (1993).
- [3] Lin, C. Y. and Chang, S. F., “A Robust Image Authentication Method Distinguishing JPEG Compression from Malicious Manipulation,” IEEE Trans. on Circuits and Systems of Video Technology, Vol. 11, pp. 153�168 (2001).
- [4] Sun, Q., Chang, S. F., Kurato, M. and Suto, M., “A New Semi-Fragile Image Authentication Framework Combining ECC and PKI Infrastructures,” IEEE International Symposium on Circuits and Systems (ISCAS 2002), Vol. 2, pp. 440�443 (2002).
- [5] Li, C. T., “Digital Fragile Watermarking Scheme for Authentication of JPEG Images,” Proc. of IEE on Vision, Image and Signal Processing, Vol. 151, pp. 460� 466 (2004).
- [6] Lu, C. S. and Liao, H. Y. M. H. Y. Mark, “Multipurpose Watermarking for Image Authentication and Protection,” IEEE Trans. Image Processing, Vol. 10, pp. 1579�1592 (2001).
- [7] Lu, Z. M., Liu, C. H., Xu, D. G. and Sun, S. H., “Semi-Fragile Image Watermarking Method Based on Index Constrained Vector Quantization,” IEE Electronics Letters, Vol. 39, pp. 36�37 (2003).
- [8] Lu, Z. M., Xu, D. G. and Sun, S. H., “Multipurpose Image Watermarking Algorithm Based on Multistage Vector Quantization,” IEEE Trans. on Image Processing, Vol. 14, pp. 822�831 (2005).
- [9] Sun, R., Sun, H. and Yao, T., “A SVD- and Quantization Based Semi-Fragile Watermarking Technique for Image Authentication,” IEEE International Conference on Signal Processing (ICSP 2002), Vol. 2, pp. 1592�1595 (2002).
- [10] Zhao, Y., Campisi, P. and Kundur, D., “Dual Domain Watermarking for Authentication and Compression of Cultural Heritage Images,” IEEE Trans. on Image Processing, Vol. 13, pp. 430�448 (2004).
- [11] Schneider, M. and Chang, S. F., “A Robust Content Based Digital Signature for Image Authentication,” Proc. of IEEE Int. Conf. on Image Processing, Vol. 3, pp. 227�230 (1996).
- [12] Cox, I. J., Kilian, J., Leighton, F. T. and Shamoon, T., “Secure Spread Spectrum Watermarking for Multimedia,” IEEE Trans. Image Process., Vol. 6, pp. 1673� 1687 (1997).
- [13] Ramkumar, M. and Akansu, Ali N., “A Robust Protocol for Proving Ownership of Multimedia Content,” IEEE Trans. on Multimedia, Vol. 6, pp. 469�478 (2004).
- [14] Celik, M. U., Sharma, G., Saber, E. and Tekalp, A. M., “Hierarchical Watermarking for Secure Image Authentication with Localization,” IEEE Trans. on Image Processing, Vol. 11, pp. 585�595 (2002).
- [15] Lin, C. H. and Hsieh, W. S., ”Applying Projection and B-spline to Image Authentication and Remedy,” IEEE Trans. on Consumer Electronics, Vol. 49, pp. 1234� 1239 (2003).
- [16] Bao, P. and Ma, X., “Image Adaptive Watermarking Using Wavelet Domain Singular Value Decomposition,” IEEE Trans. on Circuits and Systems for Video Technology, Vol. 15, pp. 96�102 (2005).
- [17] Zhou, X., Duan, X. and Wang, D., “A Semi-Fragile Watermark Scheme for Image Authentication,” IEEE International Conference on Multimedia Modeling, pp. 374�377 (2004).
- [18] Lu, C. S. and Liao, H. Y., “Structural Digital Signature for Image Authentication: An Incidental Distortion Resistant Scheme,” IEEE Transaction on Multimedia, Vol. 5, pp. 161�173 (2003).
- [19] Feng, W. and Liu, Z. Q., “Bayesian Structural Content Abstraction for Image Authentication,” Proc. of IEEE Int. Conf. on Machine Learning and Cybernetics, Vol. 7, pp. 3999�4003 (2004).
- [20] El-Din, S. N. and Moniri, M., “Hierarchical Signatures for Semi-Fragile Image Authentication with Localization,” Proc. of IEE Int. Conf. on Visual Information Engineering, pp.317�320 (2003).
- [21] Ho, C. K. and Li, C. T., “Semi-Fragile Watermarking Scheme for Authentication of JPEG Images,” Proc. of IEEE Int. Conf. on Information Technology: Coding and Computing, Vol. 1, pp. 7�11 (2004).
- [22] Wu, Y., “Detecting Tampered Image Blocks Using Error Correcting Code,” Proc. of IEEE Int. Conf. on Multimedia and Expo, Vol. 3, pp. 2047�2050 (2004).
- [23] Li, C. T., “Digital Fragile Watermarking Scheme for Authentication of JPEG Images,” Proc. of IEE on Vision, Image and Signal Processing, Vol. 151, pp. 460� 466 (2004).
- [24] Rafael, C. Gonzalez and Richard, E. Woods, Digital Image Processing, Prentice Hall.
- [25] Li, Z.-N. and Drew, M. S., Fundamentals of Multimedia, Prentice Hall.