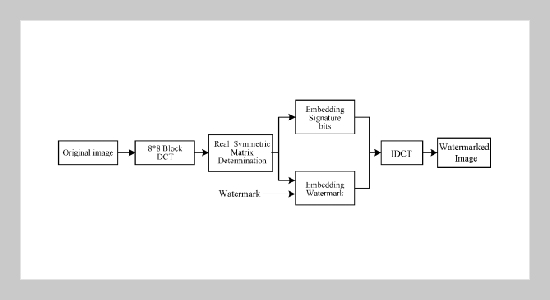
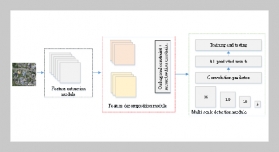
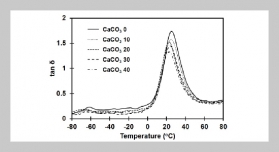
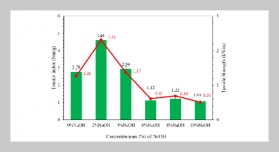
REFERENCES
- [1] Kundur, D. and Hatzinakos, D., “Digital Watermarking for Telltale Tamper Proofing and Authentication,” in Proceedings of IEEE Digital Object Identifier, Vol. 87, pp. 1167�1180 (1999).
- [2] Lin, E. T. and Delp, E. J., “A Review of Fragile Image Watermarks,” in Proceedings of the Multimedia and Security Workshop, pp. 25�29 (1999).
- [3] Lin, C. Y. and Chang, S. F., “Semi-Fragile Watermarking for Authenticating JPEG Visual Content,” in Proceeding of the SPIE, Security and Watermarking of Multimedia Contents, pp. 140�151 (2000).
- [4] Maeno, K., Sun, Q., Chang, S. F. and Suto, M., “New Semi-Fragile Image Authentication Watermarking Techniques Using Random Bias and Non-Uniform Quantization,” in Proceedong of the SPIE, Security and Watermarking of Multimedia Contents, pp. 659�670 (2002).
- [5] Nakai, Y., “Multivalued Semi-Fragile Watermarking,” in Proceeding of the SPIE, Security and Watermarking of Multimedia Contents, pp. 671�678 (2002).
- [6] Lu, C. S. and Liao, L. Y. M., “Multipurpose Watermarking for Image Authentication and Protection,” IEEE Transactions on Image Processing, Vol. 10, pp. 1579�1592 (2001).
- [7] Sun, Q., Chang, S. F., Maeno, K. and Suto, M., “A New Semi-Fragile Image Authentication Framework Combining ECC and PKI Infrastructures,” in Proceedings of the IEEE Circuits and Systems, pp. 440�443 (2002).
- [8] Fridrich, J., “A Hybrid Watermark for Tamper Detection in Digital Images,” in Proceedings of the Signal Processing and Its Applications, pp. 301�304 (1999).
- [9] Wong, P. W., “A Public Key Watermark for Image Verification and Authentication,” in Proceedings of the ICIP, Vol. 2, pp. 427�431 (1998).
- [10] Coppersmith, D., Mintzer, F., Tresser, C., Wu, C. W. and Yeung, M. M., “Fragile Imperceptible Digital Watermark with Privacy Control,” in Proceedings SPIE, Security and Watermarking of Multimedia Contents, pp. 79�84 (1999).
- [11] Dittmann, J., Steinmetz, A. and Steinmetz, R., “Content-Based Digital Signature for Motion Pictures Authentication and Content-fragile Watermarking,” in Proceedings of IEEE Multimedia Computing and Systems, Vol. 2, pp. 209�213 (1999).
- [12] Wolfgang, R. B. and Delp, E. J., “Fragile Watermarking Using the VW2D Watermark,” in Proceedings of SPIE, Security and Watermarking of Multimedia Contents, pp. 204�213 (1999).
- [13] Yin, P. and Yu, H. H., “A Semi-Fragile Watermarking System for MPEG Video Authentication,” in Proceedings of IEEE ICASSP, pp. 3461�3464 (2002).
- [14] Chen, T., Wang, J. and Zhou, Y., “Combined Digital Signature and Digital Watermark Scheme for Image Authentication,” in Proceedings of Info-tech and Infonet, pp. 78�82 (2001).
- [15] Yu, G. J., Lu, C. S., Liao, H. Y. M. and Sheu, J. P., “Mean Quantization Blind Watermarking for Image Authentication,” in Proceedings of Image Processing, pp. 706�709 (2002).
- [16] Kim, H. S. and Lee, H. K., “Invariant Image Watermark Using Zernike Moments,” IEEE Transactions on Circuits and Systems for Video Technology, pp. 766� 775 (2003).
- [17] Xin, Y., Liao, S. and Pawlak, M., “A Multibit Geometrically Robust Image Watermark Based on Zernike Moments,” in Proceedings of Pattern Recognition, pp. 861�864 (2004).
- [18] Liu, H., Lin, J. and Huang, J., “Image Authentication Using Content Based Watermark,” in Proceedings of IEEE Circuits and Systems, pp. 4014�4017 (2005).
- [19] Farzam, M. and Shirani, S., “A Robust Multimedia Watermarking Technique Using Zernike Transform,” in Proceedings of IEEE Multimedia Signal Processing, pp. 529�534 (2004).
- [20] Chen, J., Yao, H., Gao, W. and Liu, S., “A Robust Watermarking Method Based on Wavelet and Zernike Transform,” in Proceedings of Circuits and Systems, pp. 173�176 (2004).